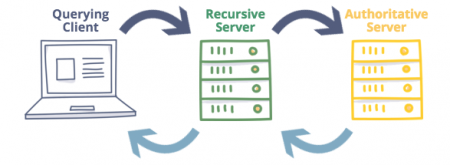
Авторитетным или первичным DNS, называют сервер на котором расположена информация о домене.
#!/bin/bash
read -p "Please enter the host IP address: " ipaddr
read -p "Please enter your domain: " domain
echo "Update the package lists..."
dnf check-update
echo "Installing BIND DNS server..."
dnf install bind -y
echo "Renaming named.conf to named.conf.bak"
mv /etc/named.conf /etc/named.conf.bak
echo "Creating new named.conf..."
cat <<EOT > /etc/named.conf
options {
listen-on port 53 { 127.0.0.1; $ipaddr; };
/* listen-on-v6 port 53 { ::1; }; */
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
secroots-file "/var/named/data/named.secroots";
recursing-file "/var/named/data/named.recursing";
allow-query { any; };
allow-transfer { none; };
recursion no;
dnssec-enable yes;
dnssec-validation yes;
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
/* https://fedoraproject.org/wiki/Changes/CryptoPolicy */
include "/etc/crypto-policies/back-ends/bind.config";
};
logging {
channel default_debug {
file "data/named.run";
severity warning;
};
};
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
include "/etc/named.zones";
EOT
echo "Creating file named.zones..."
cat <<EOT > /etc/named.zones
zone "$domain" {
type master;
file "master/$domain.zone";
allow-transfer { none; };
allow-update { none; };
};
EOT
echo "Creating forward zone for domain: $domain..."
mkdir /var/named/master
cat <<'EOT' > /var/named/master/$domain.zone
$TTL 1D
EOT
cat <<EOT >> /var/named/master/$domain.zone
@ IN SOA ns1.$domain. root.$domain. (
1 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
IN NS ns1.$domain.
@ IN A $ipaddr
ns1 IN A $ipaddr
www IN CNAME $domain.
EOT
echo "Enable and start named.service"
systemctl enable --now named
echo "Opening dns ports..."
firewall-cmd --zone=public --add-port=53/tcp
firewall-cmd --zone=public --add-port=53/udp
firewall-cmd --runtime-to-permanent
firewall-cmd --reload